
25
WWW.7X24EXCHANGE.ORGthe trade-off between the
advantages and disadvantages of
both methods can be challenging, but
careful consideration of the target
environment can help reach a
strategic decision. in eCC’s linux-
based hpC environment, we rely on
agentless ssh-based monitoring,
which we believe can provide all of
the necessary monitoring
requirements with the least
administrative overhead.
E. SCALABILITY
another important metric to consider
when acquiring a monitoring solution
is scalability, which determines the
number of devices it can monitor.
there are several factors affecting the
scalability of bsM solutions. the most
common factor is the number of
monitors applied coupled with the
number of managed devices. it is
expected that increasing the number
of monitors on each of the managed
devices decreases the number of
devices monitored by the solution.
such limitation is influenced by the
technique used for monitoring.
there are different approaches
practiced to address the scalability
limitations of bsM solutions. the most
commonly used is the distributed
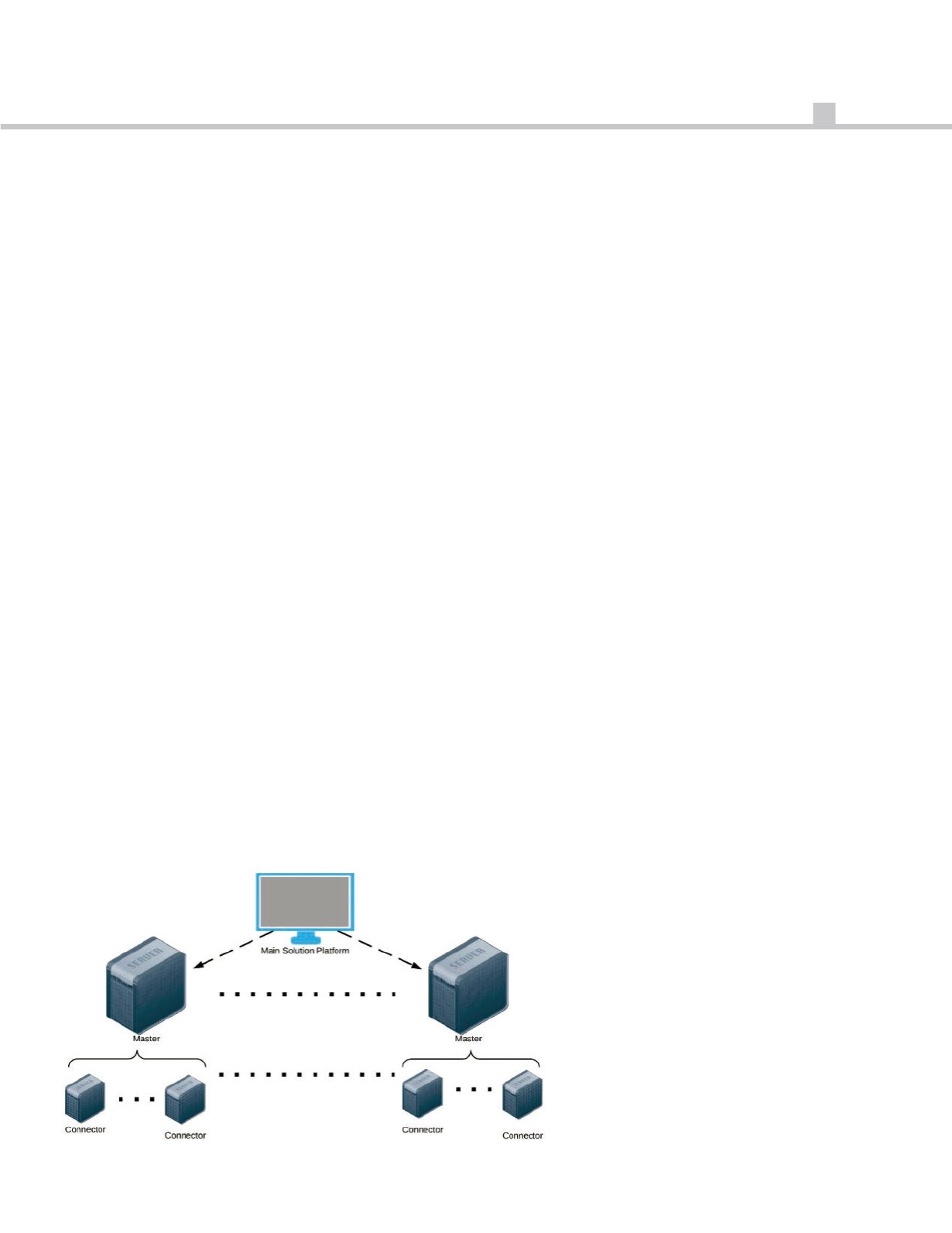
monitoring approach. in this
architecture, the solution is deployed
in different identical servers (slaves), in
which each slave is responsible for a
certain amount of the load. a master
server is deployed on top of these
slaves, which interacts and manages
the slaves. in addition, it acts as the
gateway to end-users, creating a
seamless environment on how the
monitoring infrastructure is deployed.
this architecture allows for greater
flexibility to scale the monitoring
solution horizontally and vertically,
without imposing certain
specifications on hardware resources
or other limitations. this architecture
must be tested and verified against
possible scalability thresholds or
limitations in order to deliver the
required optimal results.
another approach is to fragment the
bsM solution into several
components based on functionality.
typically, these solutions consist of a
software package to monitor network
devices, a package for monitoring
servers, a package for application
monitoring, and another package for
reporting. although such architecture
might have a solution for scalability
limitations, it also introduces several
complexities, administrative
overhead, as well as additional costs.
F. SECURITY
data is the most important intellectual
asset of any data center. thus,
maintaining a secure environment for
this data is as important as the data
itself. by deploying a new bsM
solution into your environment, it
implies that a new component will
have access to your it assets,
including stored data. this access is
required by such solutions to run the
necessary monitoring and
management tasks. understanding
how the solutions do each task, and
what access is associated with it is
essential. there are cases where the
solution is not aligned with an existing
security standard or regulation. in
addition, some solutions might
require unnecessary authority to
access some systems, in which there
are alternatives. Moreover, an agent-
based solution might introduce
additional security concerns and
require further efforts to perform
patching tasks.
thus, it is important to have a
complete understanding how each
monitoring task is performed by the
bsM solution. this includes, but is not
limited to: access privileges and
protocol required, files to be
accessed, processes run by the
software, and whether there is
outbound traffic forwarded to outside
servers. for example, a read-only ssh
access to system related files for
linux/uniX based systems is
considered a best practice method of
performing comprehensive
monitoring without compromising
security measures.
G. FRAGMENTED VS. UNIFIED
to cater to the capabilities required to
monitor the different computing
resources, bsM solutions can be
categorized into two distinct types:
fragmented and unified. a
fragmented bsM solution consists of
several function-based and
independent software applications.
each of the applications delivers a
monitoring function and works
independently from other
Figure 2 : Typical Distributed Monitoring Architecture.

















